seven stages of a cyberattack
Seven Stages of a Cyberattack!
There are seven stages of a cyberattack!
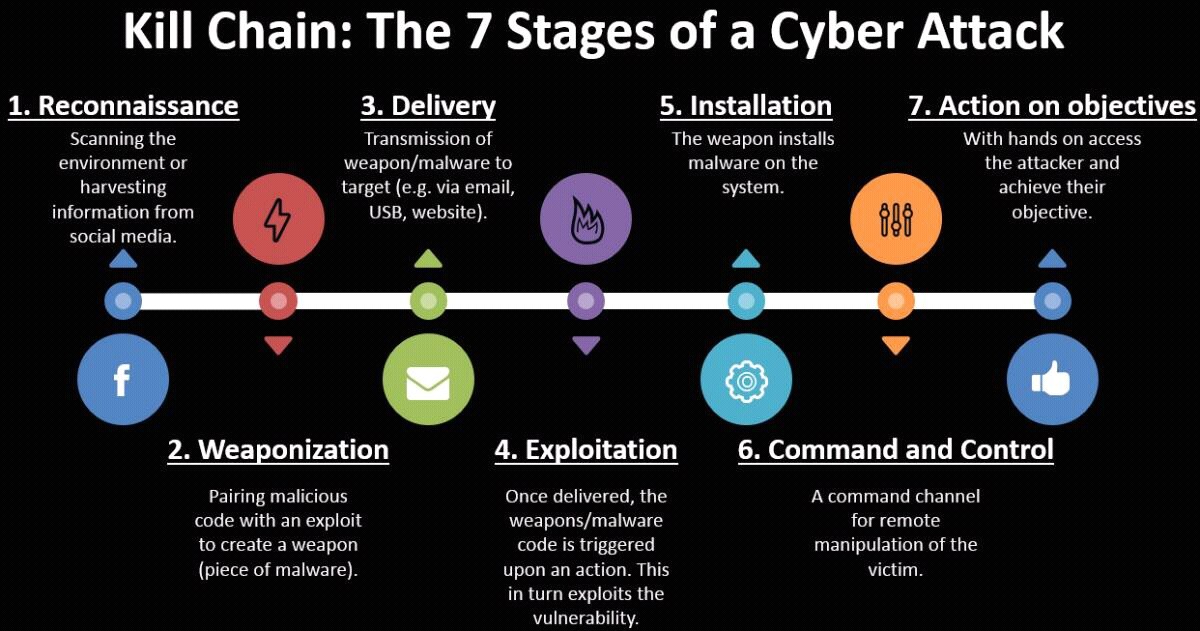
1- Hackers identify their target: Hackers only need a single point of entry to a company. Anyone including you can be the initial target.
2- Weaponizing information: The hackers use all the info they’ve gathered to create a believable phishing email or watering holes. Fake web pages that capture usernames and passwords.
3- Delivering the attack: After hackers send phishing emails or launch fake web pages, They wait for someone to send them data. will be you!
4- Exploiting the breach: The attacker then tries out the harvested usernames and passwords or remotely accesses computers through malware.
5- Installing a backdoor: The hackers ensure continued access to the network. They may create new administrator accounts, or disable firewall rules.
6- Command and control: Hackers can now impersonate people on the network – even the CEO
or they can lock all users out of the IT systems and demanding a ransom for re-entry.
7- Achieving the objectives: This could involve stealing monetizable data or incriminating emails or simply causing chaos by shutting down systems or equipment.
Ahmed Malik
Advisor to ASC/ITC & Cisco, Microsoft, Huawei Certified Instructor
Call or WhatsApp +923321569949